"Warning" to SSH users!
August 13, 2019
Okay, not to worry. There is no such actual warning. :D
I am just trying to extend my previous post on securing SSH by adding another one-liner (actually it was one liner before I decided to implement it with ansible again) solution to it.
And the solution is:
You can add "warning banners" for the incoming nodes which are trying to establish a SSH connection to your concerned nodes. These banners will give a proper insight of the guidelines and the measures, the authorities are imposing on users to ensure their server's safety and security.
me :P
- Expanding the same ansible playbook we built in the last post, edit the file "/playbook/ssh/tasks/main.yml" to add the following lines in there.
- The new tasks will do the following:
- Find the line "#Banner none" in sshd_config file and replacing it with "Banner /etc/issue".
- Copy the contents of "ssh/templates/issue" file to remote node's "/etc/issue" file.
- And finally restart the ssh service daemon again to reflect the changes.
- The new tasks will do the following:
- regexp: "^#?Banner none"
line: "Banner /etc/issue"
- name: Copy the banner issue file in remote node
copy:
src: /etc/ansible/playbooks/ssh/templates/issue
dest: /etc/issue
owner: root
group: root
mode: 0644After adding the above lines, the actual "ssh" ansible role will now look like this:
---
# tasks file for ssh
- name: Add local public key for key-based SSH authentication
authorized_key:
user: ""
state: present
key: ""
with_fileglob: public_keys/*.pub
- name: Harden sshd configuration
lineinfile:
dest: /etc/ssh/sshd_config
regexp: ""
line: ""
state: present
with_items:
- regexp: "^#?PermitRootLogin"
line: "PermitRootLogin no"
- regexp: "^^#?PasswordAuthentication"
line: "PasswordAuthentication no"
- regexp: "^#?AllowAgentForwarding"
line: "AllowAgentForwarding no"
- regexp: "^#?AllowTcpForwarding"
line: "AllowTcpForwarding no"
- regexp: "^#?MaxAuthTries"
line: "MaxAuthTries 2"
- regexp: "^#?MaxSessions"
line: "MaxSessions 2"
- regexp: "^#?TCPKeepAlive"
line: "TCPKeepAlive no"
- regexp: "^#?UseDNS"
line: "UseDNS no"
- regexp: "^#?AllowAgentForwarding"
line: "AllowAgentForwarding no"
- regexp: "^#?Banner none"
line: "Banner /etc/issue"
- name: Copy the banner issue file in remote node
copy:
src: /etc/issue
dest: /etc/issue
owner: root
group: root
mode: 0644
- name: Restart sshd
systemd:
state: restarted
daemon_reload: yes
name: sshd
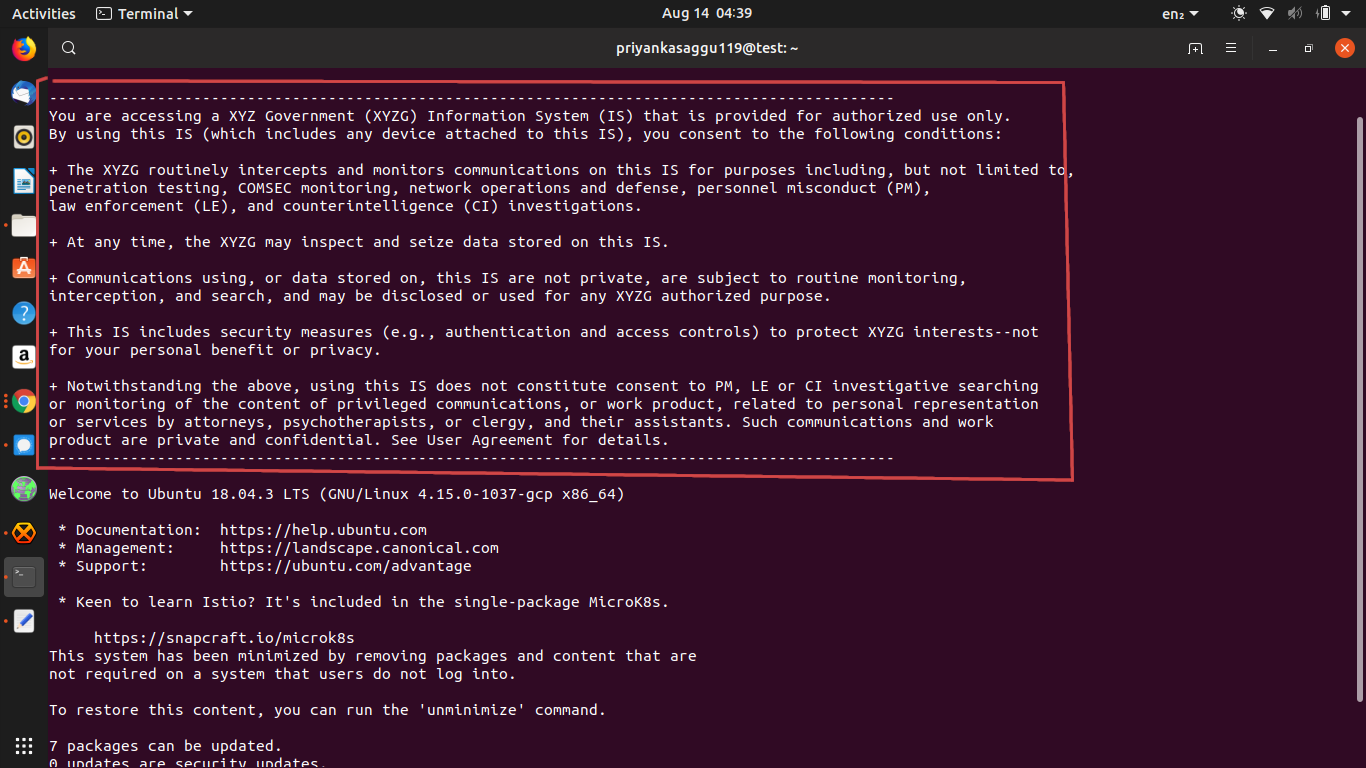
...- The contents of "/etc/ansible/playbooks/ssh/templates/issue" can be written like the following example template (This example template is taken from here.)
----------------------------------------------------------------------------------------------
You are accessing a XYZ Government (XYZG) Information System (IS) that is provided for authorized use only.
By using this IS (which includes any device attached to this IS), you consent to the following conditions:
+ The XYZG routinely intercepts and monitors communications on this IS for purposes including, but not limited to,
penetration testing, COMSEC monitoring, network operations and defense, personnel misconduct (PM),
law enforcement (LE), and counterintelligence (CI) investigations.
+ At any time, the XYZG may inspect and seize data stored on this IS.
+ Communications using, or data stored on, this IS are not private, are subject to routine monitoring,
interception, and search, and may be disclosed or used for any XYZG authorized purpose.
+ This IS includes security measures (e.g., authentication and access controls) to protect XYZG interests--not
for your personal benefit or privacy.
+ Notwithstanding the above, using this IS does not constitute consent to PM, LE or CI investigative searching
or monitoring of the content of privileged communications, or work product, related to personal representation
or services by attorneys, psychotherapists, or clergy, and their assistants. Such communications and work
product are private and confidential. See User Agreement for details.
----------------------------------------------------------------------------------------------So, now, after implementing the new modified ansible playbook again, if someone tries to establish a SSH connection to our concerned nodes, they will be welcomed with a warning banner like this.
I found this small approach towards SSH security, very interesting, thus, writing it down here.
That's all for this short post. Hope it helps!
Till next time, o/